System |
Description |
Primary Function |
Security Challenges |
Security Best Practices |
|
Industrial control system (ICS) |
Hardware and software that interface directly with physical processes. |
Control manufacturing lines, power generation, and critical infrastructure with real-time monitoring. |
Legacy systems with decades-long lifecycles, often with minimal built-in security. |
Implement thorough asset inventory. Use data diodes for unidirectional communication. Deploy passive monitoring solutions. |
|
Supervisory control and data acquisition (SCADA) |
Centralized systems that monitor and control distributed assets. |
Gather data from remote locations across large geographic areas, enabling supervision with minimal human intervention. |
Distributed nature makes network boundary protection difficult. Often uses proprietary protocols. |
Segment control networks. Implement secure remote access. Monitor for anomalous commands. |
|
Industrial internet of things (IIoT) |
Connected industrial devices with advanced connectivity and analytics. |
Collect operational data at scale for predictive maintenance and process optimization. |
Massive attack surface with numerous endpoints, often with limited computing power for security. |
Implement device authentication. Use encrypted communications. Establish zero-trust access policies. |
OT Cybersecurity
Safeguarding the Systems that Run Our World
Contents
Introduction
Protecting Industrial Systems in an Increasingly Connected World
The manufacturing floor goes silent. Production lines grind to a halt. Employees stand by helplessly as screens display ransom demands. This nightmare scenario is becoming increasingly common as cybercriminals set their sights on operational technology (OT).
73% of organizations polled in one survey suffered a cyberattack in 2024, up from 49% in 2023. Clearly, the stakes have never been higher for organizations that rely on industrial control systems.
What is OT Cybersecurity?
What is OT Cybersecurity?
OT cybersecurity is an umbrella term for the specialized measures, technologies, and practices designed to protect industrial networks from cyber threats. This includes dedicated intrusion detection systems (IDS) and ruggedized OT network monitoring solutions.
Tools like these help secure the hardware and software organizations use to monitor and control infrastructure, processes, and devices in industrial environments.
Unlike IT systems, which manage data, OT systems interact with physical processes – everything from manufacturing lines to power grids. OT cybersecurity protects these critical industrial systems that operate at each level of the control hierarchy – from field devices to enterprise integration layers.
Understanding OT Systems: ICS vs. SCADA vs. IIoT
The OT Cybersecurity Threat Landscape
The threat landscape for industrial systems has evolved dramatically in recent years, with events like the 2021 Colonial Pipeline attack highlighting the growing risks to global industry. What was once theoretical has become an operational reality for many organizations.
A Growing Threat
Financial Implications
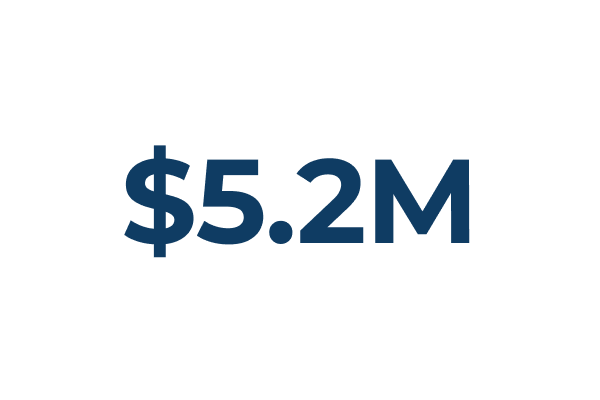
Average cost per incident from operational downtime (IBM & the Ponemon Institute)
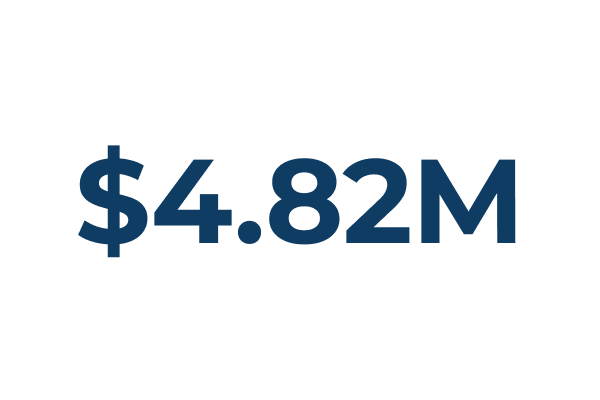
Average cost of a critical infrastructure breach (IBM & the Ponemon Institute)
For specific industries, like automotive manufacturing, downtime costs can reach $2.3 million per hour. That's equivalent to $600+ per second of lost production.
Understanding how to properly segment and secure industrial networks is essential for mitigating these growing risks. This is where the Purdue Model provides critical guidance for creating effective OT security architectures.
Why OT Cybersecurity is Critical
The convergence of IT and OT, combined with increasingly sophisticated threat actors, has created a perfect storm for industrial organizations.
Increased Attack Surface
As OT systems connect to business networks and the internet, they expose previously isolated systems to a wider range of threats.
More Sophisticated Attackers
Both criminal groups and nation-state actors have developed advanced capabilities specifically targeting industrial systems. Cybersecurity experts discovered three new ICS-capable malware strains in 2024: FrostyGoop, IOControl, and Fuxnet.
Aging Infrastructure
Many industrial systems were designed for operational reliability, not security. Legacy equipment with decades-long lifecycles lacks modern security features, making it vulnerable to attacks.
Physical Consequences
OT security breaches can have a direct impact on physical processes and systems, making them potentially more damaging the an IT system breach. 1,015 sites experienced physical consequences from cyberattacks in 2024, up from 412 in 2023.
7 Essential Components of OT Cybersecurity
A robust OT cybersecurity strategy includes several elements that work together to create multiple layers of protection.
1. Network Visibility and Monitoring
Complete network visibility is the foundation of effective OT security. Only 5% of organizations reported 100% OT system visibility in 2024, down from 10% in 2023 and 13% in 2022 – a concerning trend as attack sophistication increases.
Specialized OT Network Monitoring solutions provide 100% visibility into traffic flows between IT and OT systems, enabling security teams to detect anomalies and potential threats before they impact operations.
2. Network Segmentation
Segmenting OT networks from IT networks using industrial demilitarized zones (IDMZs) and implementing zero-trust principles for cross-domain communications creates multiple layers of protection. This makes it harder for attackers to move laterally between networks if they gain initial access.
Internal network segmentation has grown significantly as a defensive measure, with 60% adoption in 2024 – up from 44% in 2023.
3. Asset Inventory and Management
Maintaining a comprehensive inventory of all OT assets, including devices, firmware versions, and communication patterns, provides the foundation for effective security. Many organizations struggle with visibility because they lack accurate knowledge of what systems are present in their environment.
4. Zero-trust Technology
Zero-trust monitoring solutions provide an extra layer of security for OT systems. Based on zero-trust technology, they remain invisible to the network, making them immune to infiltration – regardless of access to stolen or corrupted credentials.
When security tools connect through these systems, they become much harder for attackers to penetrate. This adds another, essential protective layer that blocks malware from entering your systems.
5. Defense in Depth
No single security measure is enough to guarantee 100% protection against cyber threats. A defense-in-depth approach implements multiple layers of controls throughout your industrial network architecture. Each layer provides an additional barrier that attackers must overcome, significantly reducing the risk of successful breaches.
Key elements include of a defense-in-depth approach include physical security controls, endpoint protection, access controls, and network monitoring.
6. Security for Physical Processes
OT security failures can have physical consequences. As such, a cyberattack could endanger human safety, environmental integrity, and critical infrastructure.
Protection strategies must prioritize operational safety and continuity. This means implementing fail-safe mechanisms that default to safe states, establishing monitoring that can detect process manipulation, and ensuring physical override capabilities exist for critical systems.
7. Incident Response
Developing specialized response procedures for OT security incidents is crucial. These procedures must prioritize operational safety and continuity while containing threats.
Unlike IT environments, where you can often take systems offline for remediation, OT incident response requires strategies that maintain critical operations while addressing security issues. This is increasingly important as 24% of intrusions targeted OT systems directly in 2024 (up from 17% in 2023).
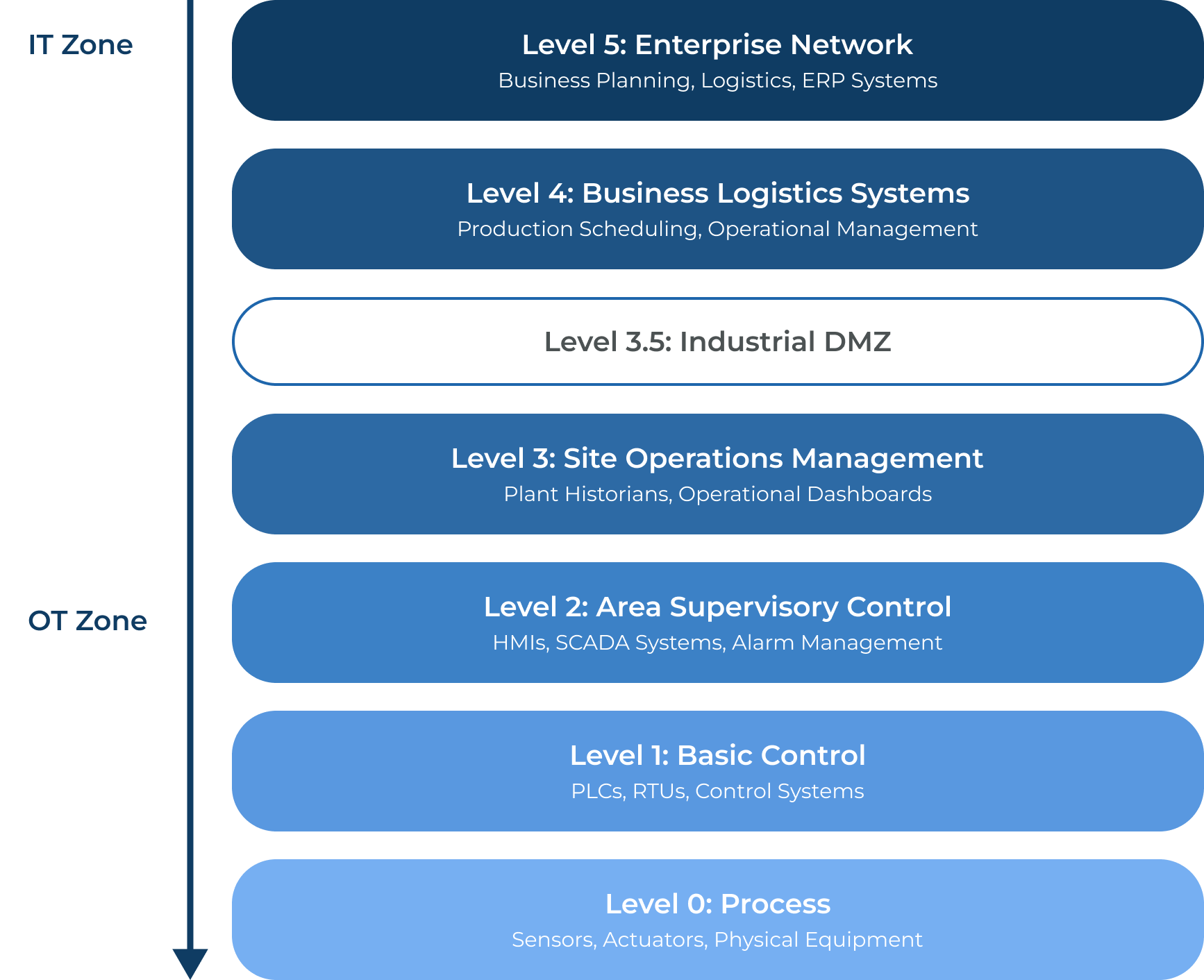
The Purdue Model: A Proven Framework for OT Security
The Purdue Model: A Proven Framework for OT Security
The Purdue Enterprise Reference Architecture (Purdue Model) provides the foundation for understanding security in industrial environments. This hierarchical model divides industrial control systems into zones and conduits, establishing clear security boundaries between five operational levels.
Level 5-4: Enterprise Zone
Business logistics systems, including enterprise resource planning (ERP) and business planning. These connect to external networks and represent the traditional IT domain.
Level 3.5: Industrial Demilitarized Zone (IDMZ)
The critical security boundary between IT and OT networks. This zone contains firewalls, data diodes, and security controls that limit traffic between business and control systems.
Level 3: Site Operations Management
Operational management systems that oversee plant-wide control functions, including historians, production scheduling, and maintenance systems.
Level 2: Area Supervisory Control
Supervisory systems that monitor and control specific process areas. These include human machine interfaces (HMIs), SCADA systems, and alarm management.
Level 1: Basic Control
Controllers that govern specific processes. For example, programmable logic controllers (PLCs), remote terminal units (RTUs), and other control systems that directly interface with physical equipment.
Level 0: Process
The physical equipment and instrumentation (sensors, actuators, motors, and similar devices) that perform industrial processes.
The IT/OT Convergence Challenge: Securing Interconnected Industrial Systems
The IT/OT Convergence Challenge: Securing Interconnected Industrial Systems
As industrial organizations embrace digital transformation, the traditional boundaries between Information Technology (IT) and Operational Technology (OT) continue to blur. This convergence represents both a strategic opportunity and a significant security challenge.
While the Purdue Model provides an excellent framework for securing traditional industrial environments, today's connected world introduces new challenges.
Enterprise systems (Levels 4-5) now connect directly to operational management systems (Level 3), creating potential pathways for threats to move between business and industrial networks. The IDMZ at Level 3.5 becomes especially critical as the primary security boundary between these worlds.
This complexity requires advanced OT network monitoring solutions that can provide visibility across boundaries – helping you identify unauthorized communications and potential threats.
Several factors add to the challenge. For example:
- Legacy OT systems with decades-long lifecycles must interoperate with rapidly evolving IT systems
- Cloud-based applications require secure connections to previously isolated control systems
- Remote access requirements introduce new entry points at multiple levels of the Purdue hierarchy
- IIoT devices create vast new attack surfaces that span traditional IT/OT boundaries
Convergence in Numbers
31% of organizations had six or more intrusions in the past year. Although the IT/OT convergence isn't entirely to blame, it's undoubtedly a key factor. To protect previously isolated systems, Fortinet encourages organizations to focus on achieving "comprehensive visibility, the ability to segment networks and protect network boundaries, and monitoring and controlling access to OT systems based on the user’s defined role."
Learning from History
The 2021 Colonial Pipeline attack demonstrates the devastating impact of IT/OT convergence vulnerabilities. Attackers gained access through an IT network virtual private network (VPN), then moved laterally into operational systems, forcing a complete shutdown that affected fuel supplies across the eastern United States for days.
How BP Protects OT Systems
How BP Protects OT Systems
One of the world's largest energy companies achieved complete network visibility across its complex OT and IT infrastructure by implementing passive fiber test access points (TAPs) and network packet brokers.
These specialized OT network monitoring solutions bridge the gap between operational demands and security requirements in mission-critical environments. Operating silently in the background, they give BP full visibility of its network without compromising performance or reliability.

Key Insights
-
Secured critical control systems without impacting operations
-
Enabled 24/7 monitoring of equipment, firmware, and network traffic
-
Reduced security risks while maintaining zero-latency
-
Achieved regulatory compliance
-
Connected multiple security and monitoring tools seamlessly
OT Cybersecurity FAQs
-
IT cybersecurity focuses primarily on protecting data confidentiality, integrity, and availability in business systems. Think email inboxes, company databases, and web applications. Key concerns include data theft, privacy breaches, and service disruptions.
OT cybersecurity prioritizes the safety, reliability, and availability of industrial control systems that manage physical processes. Key concerns include damage to process-critical equipment, production stoppages, operator safety hazards, and environmental risks.
-
An OT security operations center (OT SOC) is a specialized facility dedicated to continuously monitoring and defending operational technology environments from cyber threats. Unlike traditional SOCs, an OT SOC focuses specifically on industrial control systems, SCADA, and other operational technologies.
Key components of an OT SOC include:
- Personnel with specialized knowledge of both industrial processes and cybersecurity
- Tools for monitoring industrial protocols, asset discovery, and anomaly detection
- Processes for responding to security incidents while maintaining operational continuity
- Intelligence about OT-specific threats and vulnerabilities
-
An OT firewall is a specialized network security device designed specifically for industrial control system environments. Unlike traditional IT firewalls, OT firewalls:
- Understand and filter industrial protocols like Modbus, DNP3, and Profinet
- Operate reliably in harsh industrial environments
- Maintain deterministic performance for time-sensitive control traffic
- Provide deep packet inspection for industrial commands to prevent malicious actions
- Function with minimal latency to avoid disrupting critical processes
Organizations typically deploy OT firewalls at the boundary between IT and OT networks (Level 3.5 in the Purdue Model) and between different security zones within the OT environment. They often include protocol conversion and data validation functions to sanitize communications between different network segments.
-
IT and OT SOCs differ primarily in their focus and priorities. IT SOCs protect information systems, with an emphasis on data confidentiality. They use standard security tools, like SIEM platforms and EDR solutions. Teams specialize in IT networks and can often respond by isolating affected systems.
By contrast, OT SOCs protect industrial control systems with safety and availability as top priorities. They require specialized expertise in industrial systems and protocols, and must carefully balance security responses against operational continuity. Unlike IT SOCs, which can often shut down compromised systems, OT SOCs must maintain critical operational processes while addressing security threats.
Take Control of Your OT Network Visibility
Get 100% traffic visibility across your industrial systems. Built for harsh environments and aligned with IEC 62443 compliance.
About Network Critical
Since 1997, Network Critical has provided flexible and intuitive monitoring solutions (network TAPs and packet brokers) for organizations across the globe.
Our talented technical teams design, develop, and manufacture all our products in-house – working alongside leading technology partners including Cisco and Dark Trace to deliver innovative networking solutions.
With offices in Europe, North America, and the Middle East, we help organizations like yours connect vital network monitoring, security, and performance tools safely. From monitoring traffic across multiple to error-free network configuration via our Drag-n-VuTM software , you'll find the tools you need to take control of your network.