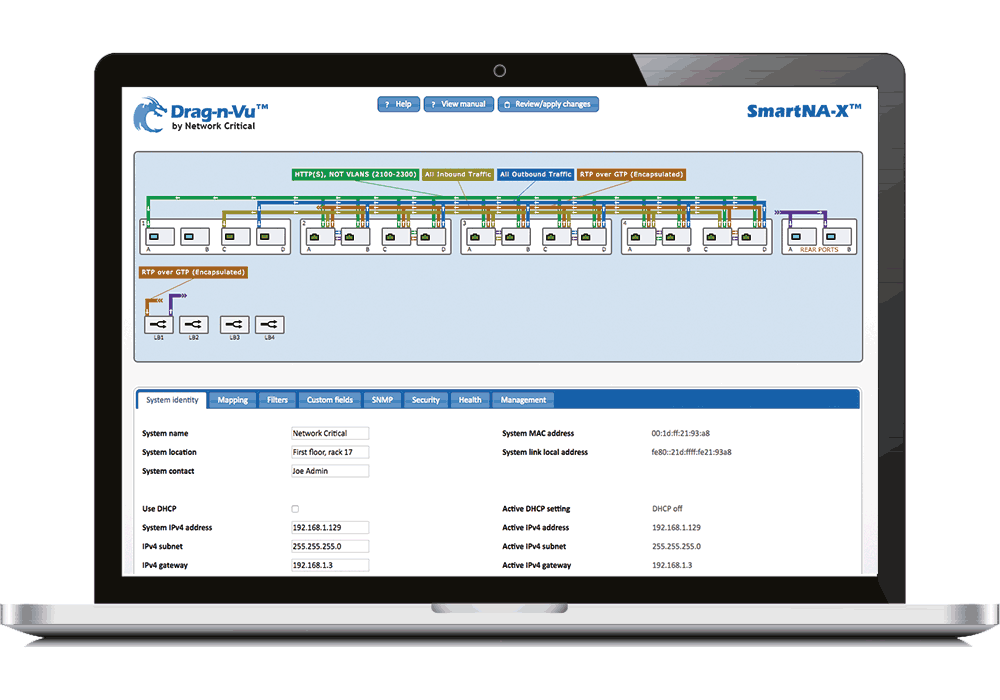
Network Critical’s revolutionary Drag-n-Vu™ is a sophisticated computational engine with an intelligent and intuitive graphical user interface that enables fast, error-free configuration and simplifies change management.
Network Management
Intelligent and intuitive GUI
An Introduction to Drag-n-Vu™
Connecting a variety of network monitoring and security tools that perform different functions and require varying subsets of network data is complicated. Even relatively simple tools like firewalls are easily misconfigured.
Manually configuring what goes into these tools and what comes out is a painfully slow, error-prone task. Mistakes in filter hierarchies or port assignments can create security vulnerabilities and service interruptions.
With Drag-n-Vu™, the painstaking planning, computation and detailed input requirements are removed. You now have complete control and visibility at your fingertips. Creating filters and mapping data to input and output ports is as easy as dragging the cursor over a graphical port representation and clicking.
See How It Works:
Enables fast, error-free configuration and simplifies change management
Significantly reduce your operational costs
Manual configuration of your security and monitoring tools is intolerably slow and subject to error. Mistakes in filter hierarchies or port assignments can create security vulnerabilities and service interruptions. The simplicity of Drag-n-Vu™ not only speeds up deployment, but reduces operational cost by allowing filter and mapping tasks to be performed by network administrators rather than engineering personnel. In network management, where change is the only constant, moving tool management downstream not only saves money but also decreases down-time during maintenance windows.
Use Cases and Features
- Simple and accurate traffic configuration to direct and
control traffic to performance and monitoring tools - Create filters and flow-based data mapping with drag-and-drop simplicity, ensuring rapid detection and
response to emerging threats - Reduce operational costs and eliminate downtime during maintenance windows without the need for specialist engineering personnel

-
Enables fast, error-free configuration and simplifies change management
-
A single-pane-of-glass network management system, at your fingertips
-
A sophisticated computational engine, with an intelligent and intuitive graphical interface
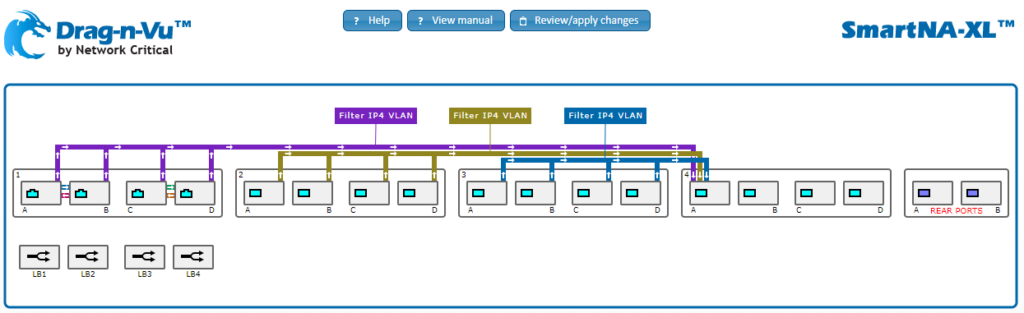
A Drag-n-Vu™ use example: aggregation and filtering
Common use example: Aggregation & Filtering End-user has a number of SPAN ports and some ethernet TAPs in their architecture and want to leverage an IDS (Intrusion Detection System) to monitor their network for malicious activity or policy violations. In the below example we are showing 3 different ways to capture data traffic:
- Module 1: This module shows 2 copper TAPs where A&C are transmit (Tx) and B&D are receive (Rx). Copies of the data traffic are pulled via the backplane, filtered for IPv4 traffic and then routed to module 4 port A
- Module 2: This module shows 4 SPAN ports coming from network devices and aggregated in the backplane, filtered for IPv4 traffic and then routed to module 4 port A
- Module 3: This module shows 4 ports connected from network TAPs and aggregated in the backplane, filtered for IPv4 traffic and then routed to module 4 port A
- Module 4: This module shows all the filtered traffic from modules 1, 2 & 3 are being aggregated and sent to an IDS tool connected to port A
This solution shows our hybrid TAP/packet broker aggregating all the traffic from different sources, applying a filter and then sending resulting data traffic to an IDS tool.
NOTE: Depending on the expected traffic volume, many end-users would enable load balancing and send multiple links to their IDS tools so no oversubscription could impact performance.