Ethernet TAPs
Crystal-Clear Visibility For Copper Networks
Strengthen security and decrease downtime with Ethernet TAPs that capture network traffic without impacting performance.

Creating a Clear Line of Sight For
100% Visibility. Zero Exposure.
- No Network Footprint
- Gain network insights through Ethernet TAPs that remain hidden from cybercriminals.
- Easily Scalable
- Deploy as standalone TAPs or within SmartNA™ chassis for advanced traffic management.
- True Visibility
- Capture every single packet – including errors and malformed frames.
- Trusted in Critical Networks
- Trusted in finance, healthcare, defense, and other high-compliance industries globally.
1Gb SmartNATM
Manage and optimize 1G network visibility with SmartNA™. Featuring plug-and-play deployment, SmartNA™ ensures efficient traffic monitoring, filtering, and load balancing – all in one compact solution.
-
Modular, scalable design
-
Zero-loss architecture
-
Intelligent traffic filtering and aggregation
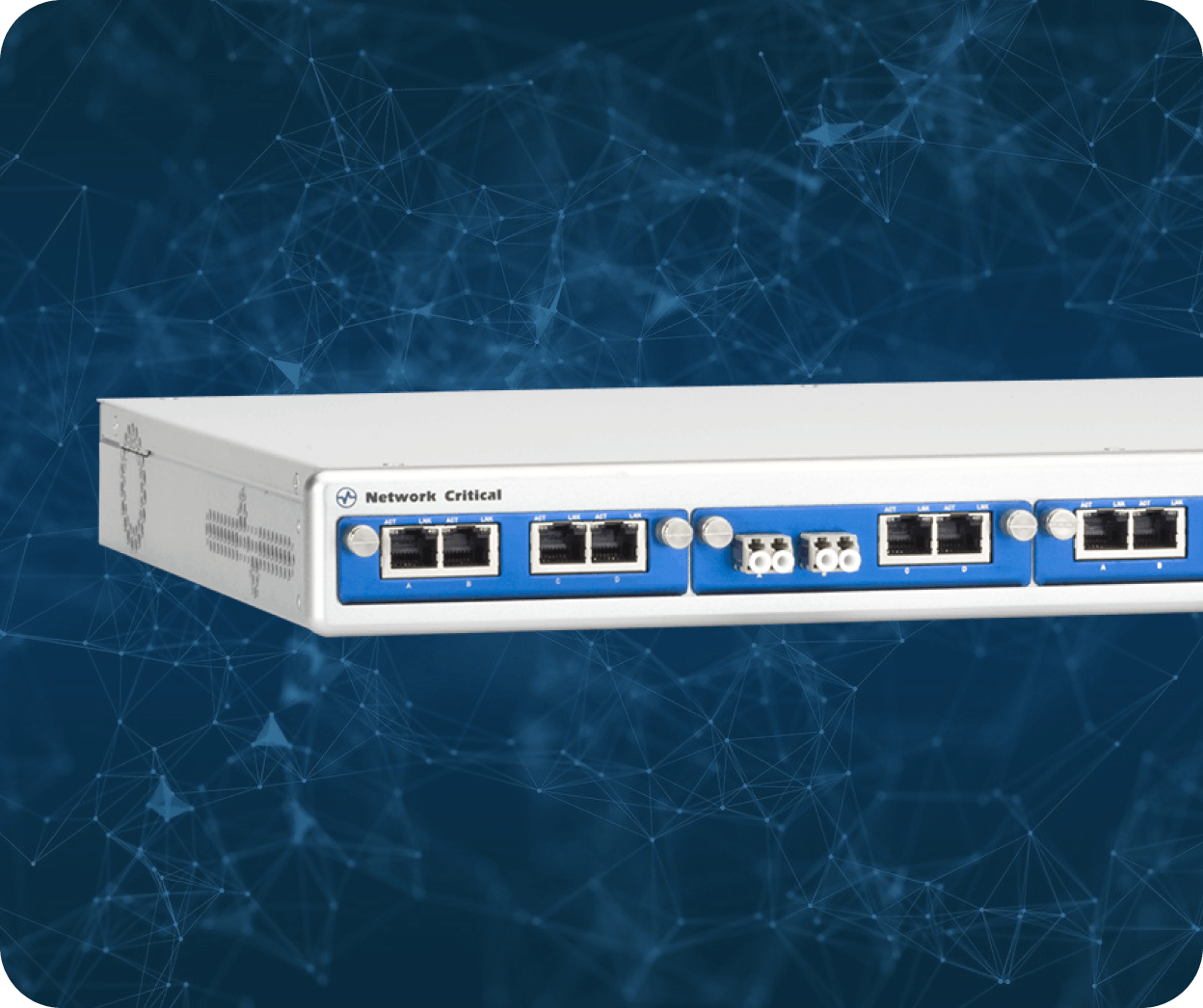
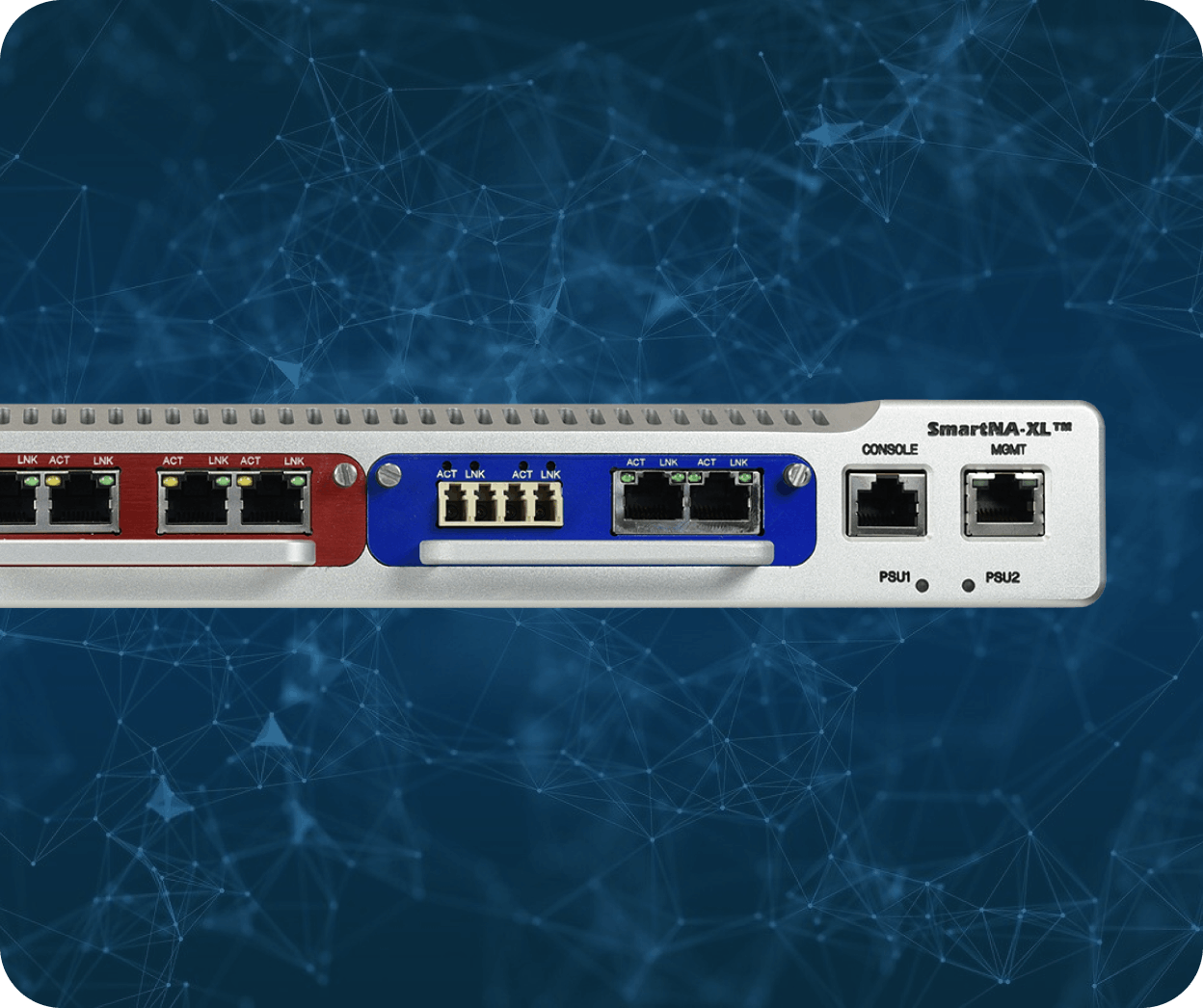
SmartNA‑XL™
Maximise network visibility with this compact and scalable hybrid TAP. The SmartNA‑XL™ delivers high-speed aggregation, filtering, and load balancing with zero packet loss and no latency.
-
Modular design supporting up to 40Gbps
-
Simplified management with Drag-n-Vu™
-
Fail-safe technology ensures zero points of failure
What Our Customers Say
“The Network Critical products are providing 100% accurate traffic visibility on the key links, which is vital for us.”
Vodafone
Network Performance Monitoring Engineer
"Network Critical’s solutions compliment HSBC’s environment perfectly - combining the zero latency with modular functionality and features to maximise their network performance reporting. This resulted in HSBC being able to continue to provide to their customers with first class service while ensuring security and efficiency."
HSBC
Senior Technical Consultant
"Continuous monitoring is critical to digitization and automation of our many monitoring systems. Being able to monitor remote sites from a single location keeps our systems up to date without having a large staff running around in trucks."

BP
Senior Project Manager, Refining Operations
Proud to Partner With
FAQs
-
The TAP automatically bypasses the tool, ensuring uninterrupted traffic flow.
-
Passive fiber TAPs don’t introduce any latency, and bypass modes add minimal overhead with high-speed switching.
-
Yes. You can deploy identical tools in active/standby mode with automatic failover.
-
Yes. You can implement L2-4 filtering, VLAN tagging, packet slicing, header stripping, and payload masking to ensure your security tools only receive relevant traffic. This significantly improves their efficiency and extends their life.



