See, Optimize, and Secure Your Entire Network
Get crystal clear insights with unhackable, high-performance network TAPs and Packet Brokers.

Dependable Network Visibility Solutions for
Take Control of Your Network
- 100% Visibility
- Spot every threat, address every vulnerability, and keep your network secure.

- 24/7 Availability
- Filter, aggregate, and balance traffic to maintain peak network performance.
- Ready in Minutes
- Deploy and configure effortlessly with our intuitive Drag-N-Vu software.
- 365 Support
- Get the help you need, when you need it – from general enquiries to technical assistance.
Adaptable Solutions for Dynamic Networks
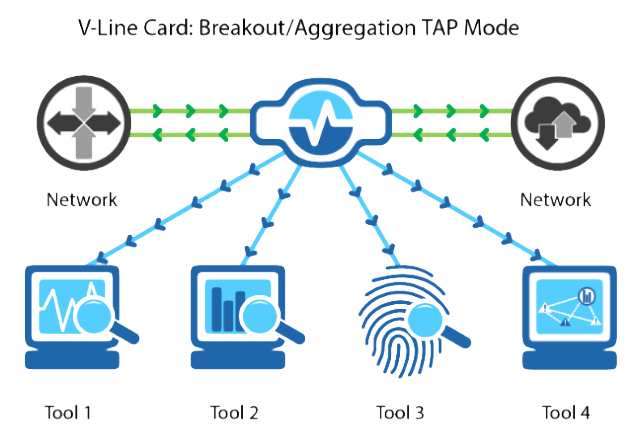
Intelligent Hybrid TAP and Packet Broker
Maximize network visibility while streamlining your monitoring architecture. The solution combines advanced traffic capture with powerful packet processing in a single unified platform, delivering 100% traffic visibility without compromising network performance.
- Advanced packet filtering and manipulation
- Modular design with hot-swappable components
- Fail-safe operation
High-density Network TAPs
Illuminate the darkest corners of your network. Whether you’re looking to improve security or performance, our SmartNA Network TAPs deliver 100% traffic capture without disrupting operations.
- Real-time visibility
- No latency
- Fully configurable
Scalable Network Packet Brokers
Optimize your network, save rack space, and reduce costs. Our network packet brokers process inputs from multiple sources, delivering the right traffic to the right tools to keep things running smoothly.
- Intelligent traffic filtering
- Zero packet loss
- Up to 400Gbps port speed access
Adaptable Bypass TAPs
Get consistent, year-round network performance. Intuitive by design, our bypass TAPs continuously monitor your network security appliances, bypassing inactive or compromized ones to keep traffic flowing and your network secure.
- Built-in fail-safes
- Advanced packet manipulation
- Dual hot-swappable power supplies
What Our Customers Say
“Latency is our enemy. Network Critical tools let us protect our network and plan for future growth by giving us accurate data without adding delay into our network.”

The Stars Group
Director, Global Network Engineering
“We chose the Network Critical equipment because of its unique functionality and for the Drag ’n Vue Graphical Interface which simplifies initial deployment and makes ongoing management fast and easy.”
.png?width=300&height=300&name=MLB%20(1).png)
Major League Baseball
Sr. Systems Engineer,Telecommunications Company
“I had great pleasure in working with HSBC and their senior network teams to create and deploy a unique global visibility network that maximizes their current and future monitoring requirements.”
HSBC
Senior Technical Consultant
“Continuous monitoring is absolutely critical to maintaining a high quality network and staying in compliance with European data regulations. Network Critical SmartNA-XL allows us to see and manage traffic without impacting live traffic.”

Vodafone
OSS Tools Manager
“Continuous monitoring is critical to digitization and automation of our many monitoring systems. Being able to monitor remote sites from a single location keeps our systems up to date without having a large staff running around in trucks.”

BP
Senior Project Manager, Refining Operations












.png)
.png)